- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- Phrack Magazine: Digital hacking magazine.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
2020. június 30., kedd
Ethical hacking : Top 10 best websites to learn hacking 2018
2020. június 11., csütörtök
DEFINATION OF HACKING
DEFINATION OF HACKING
Hacking is an attempt to exploit a computer system vulnerabilities or a private network inside a computer to gain unauthorized acess.
Hacking is identifying and exploiting weakness in computer system and/ or computer networks for finding the vulnerability and loopholes.
Related linksHacking is an attempt to exploit a computer system vulnerabilities or a private network inside a computer to gain unauthorized acess.
Hacking is identifying and exploiting weakness in computer system and/ or computer networks for finding the vulnerability and loopholes.
- Pentest Aws
- Pentest Wordpress
- Pentest With Metasploit
- Pentest Linux
- Hacking Images
- Hacking Gif
- Hacking Programs
- Hacking Tools
- Pentest Certification
- Hacking Health
- Hacker Kevin Mitnick
- Hacker Language
- Pentester Academy
- Pentest Windows 7
- Hacking With Raspberry Pi
- Hacker Kevin Mitnick
- Hacking Simulator
- Hacking Device
- Pentest Security
- Pentest Training
How To Repair A Crashed SD Card And Protect Your Data
One of the many reasons users prefer Android devices is the ability to expand the amount of available storage space using the MicroSD Card. Since we have the ability add up to 256GB of external storage to Android devices today, you're bound to choke up when the SD card crashes without any tell-tale signs.
If you're experiencing issues on how to repair a crashed SD card on your Android device, there are certain fixes you can try out. Since there's not a singular solution to SD Card issues, we've created a guide to help you detect the issue with your external storage and mentioned multiple solutions to get your SD card working and even retrieve your stored data along with it.

Before you start
Before you start
Don't format the card if you want to retain any of the photos on it. You can follow the tips in our separate article on how to format a write-protected SD card after you've tried to recover any files that are on your card.
Now, try and find a different card reader. If you've inserted an SD card into your laptop or PC's built-in slot and nothing happens, try using a different computer or a USB card reader.
Read More;- Hacking Gmail For Free Custom Domain
Sometimes it's the reader at fault – not the card. You can buy a USB SD card reader online for just a couple of pounds which will accept both microSD and standard SD cards.
Steps to Repair a Crashed SD Card and Protect your Data:
Step 1 – Physically clean the SD Card
Despite being durable and built to last, SD cards are prone to crashing sometimes due to physical damage. Since you carry your phone around everywhere, some dirt and dust are bound to fill up in the cracks, that can make SD card stop working from time to time.
The first thing you can try to do on how to repair a crashed SD card is physically scrub and clean it.
- Remove the MicroSD card from your Android device and place it on a clean surface. Make sure that you turn off your phone before pulling out the SD card for safety.
- Flip the MicroSD card and using a white eraser, gently scrub the gold contact pins of the SD card to get rid of any residual dirt or grime.
- If you have an alcohol-based cleaning solution or even nail polish remover around, dab it on to the connector pins using a Q-tip and gently rub it.
Once the SD card has dried out, you can plug it back into your Android device and turn it on to see if the solution has worked.
Also Read;- How To Get Grammarly Premium Account Free 2018
Step 2 – Format the SD Card
If your SD card is being detected by the Android device but you're having trouble accessing the saved files, there's a good chance that the files are corrupt. This could either be due to a particular broken file in the saved storage, or a virus that is causing the issue.
Either way, the only option there is left for you to try out is make the SD card reusable for formatting it.
- From the home screen of your Android device, head over to the Settings app and then scroll down to find the Storage
- In the Storage tab, you'll be able to find the Erase SD Card option, so go ahead and select it.
- Confirm your action to delete all of the files and folders stored on your SD card and this should effectively solve the issue.
Step 3 – Check the SD card compatibility
If you are trying to figure out how to repair a crashed SD card on an older Android device, you might just need to look at the details more carefully. If your SD card fails to be recognized on the mobile device but works with your computer, the problem could be related to compatibility.
Also Read;- How To Install and Run Backtrack On Android
- If the MicroSD card that you are trying to use with your older phone is SDXC version (built for higher transfer speeds), it will not be recognized.
- Look up the maximum capacity of expandable storage that is supported by your device, since they can vary from starting at 64GB to all the way up to 256GB.
Step 4 – Diagnose the SD card using a PC
If a simple format did not help you solve the SD card problem, you might need a more technical analysis of the issue. To do so, you can plug in your SD card into a computer and use the diagnostic tools to find out the pertaining errors and effectively fix them.
- Connect your Android mobile device to a computer using a USB cable.
- Make sure that you connect Android as MSC (Mass storage mode) and not MTP (Media transfer mode). You can do this using the notification menu once you connect the phone to your computer.
- Launch the Windows Explorer and right click on the SD card driver you see on the screen. In the options menu, choose Properties – Tools – Error Checking and wait for the entire process to complete.
- The computer will try to update the software for your SD card and fix any errors that are causing it to crash.
Step 5 – Use chkdsk to fix/repair a corrupted SD card without data loss
The "chkdsk" command is your first choice for damaged SD card repair. Requiring no format, it allows you to fix or repair a corrupted SD card and regain access to all your important files on the device. Let's see how it works. (I'm using Windows 7 for this demonstration)
1. Plug in your SD card to your computer with a card reader.
2. Go to the start menu, type in "cmd" in a search bar, hit enter and then you can see something named "cmd. exe" in a list of programs.
3. Right-click "cmd. exe" and then you will get the following command windows that allow you to fix your corrupted SD card without formatting.
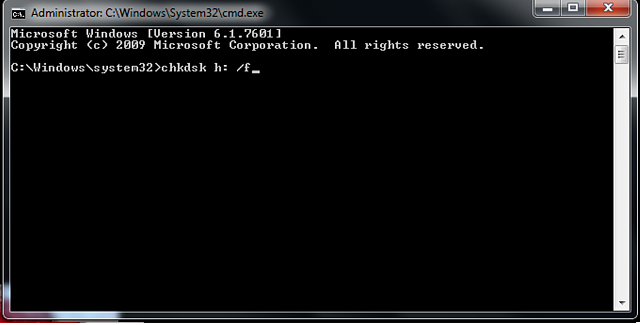
4. Type in "chkdsk /X /f sd card letter:" or "chkdsk sd card letter: /f ", for example,"chkdsk /X /f G:" or "chkdsk h: /f".
After finishing all the steps, Windows will have checked and fixed the file system of the SD card. It usually takes several minutes. After that, if you see "Windows has made corrections to the file system" in the command window, then congratulations! The damaged SD card is successfully fixed and you can see your data again. If not, you should try a third-party data recovery software to retrieve your files from the damaged SD card and repair it by formatting.
Once the process has been completed, you can go ahead and pop the SD card back into your Android device and see if the issue has been resolved.
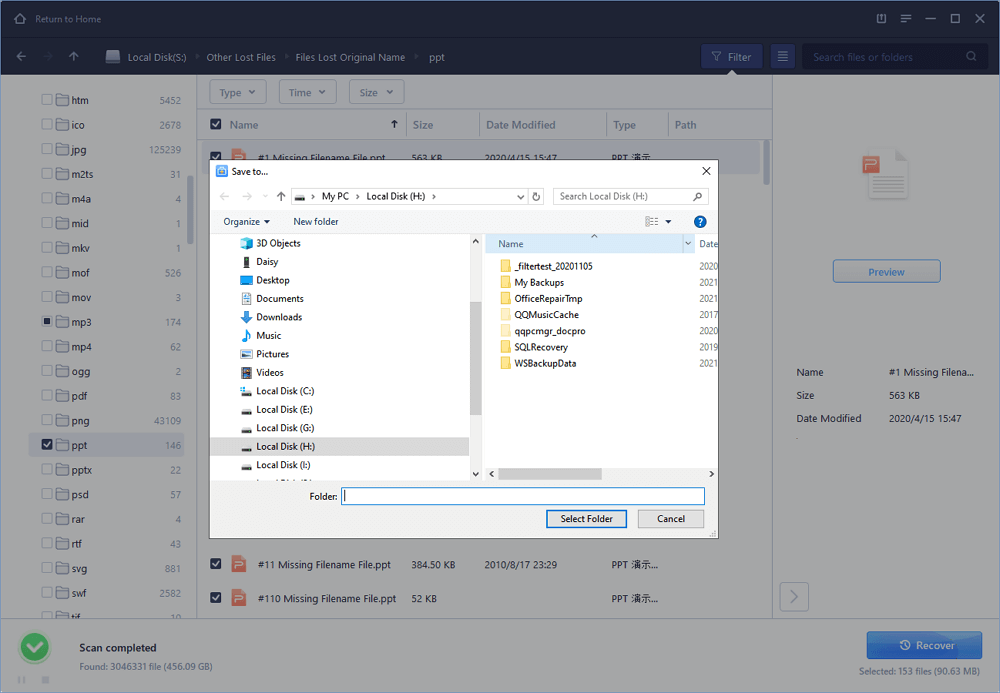
Step 6 : Use EaseUS Data Recovery Wizard to recover data from damaged SD card
1. Connect the corrupted SD card to your PC, launch EaseUS's data recovery software, select the card and click "Scan".
2. A quick scan will first start to search all the lost and existing data on the SD card. And after that, a deep scan will automatically launch in order to find more files.
2. A quick scan will first start to search all the lost and existing data on the SD card. And after that, a deep scan will automatically launch in order to find more files.
3. After the scan, choose those files you want to recover and click the "Recover" button to retrieve them back.
Final Words :
So finally through this article, you have got to know about the method by which the SD card could be repaired and hence the data in it could be saved for the further access. We have tried to present the method in easy to grab manner and we believe that you could possibly get to know about it easily. Hope that you would have liked the information in this post, if it is so then please share it with others. Also, do not forget to share the post with others, let most of the people know about the method. Share your comments about the post through using the comment box below. At last never the fewer thanks for reading this post!
Related links
Steghide - A Beginners Tutorial
All of us want our sensitive information to be hidden from people and for that we perform different kinds of things like hide those files or lock them using different softwares. But even though we do that, those files attractive people to itself as an object of security. Today I'm going to give you a slight introduction to what is called as Steganography. Its a practice of hiding an informational file within another file like you might have seen in movies an image has a secret message encoded in it. You can read more about Steganography from Wikipedia.
In this tutorial I'm going to use a tool called steghide, which is a simple to use Steganography tool and I'm running it on my Arch Linux. What I'm going to do is simply encode an image with a text file which contains some kind of information which I don't want other people to see. And at the end I'll show you how to decode that information back. So lets get started:
Requirements:
1. steghide
2. a text file
3. an image file
After you have installed steghide, fire up the terminal and type steghide
It will give you list of options that are available.
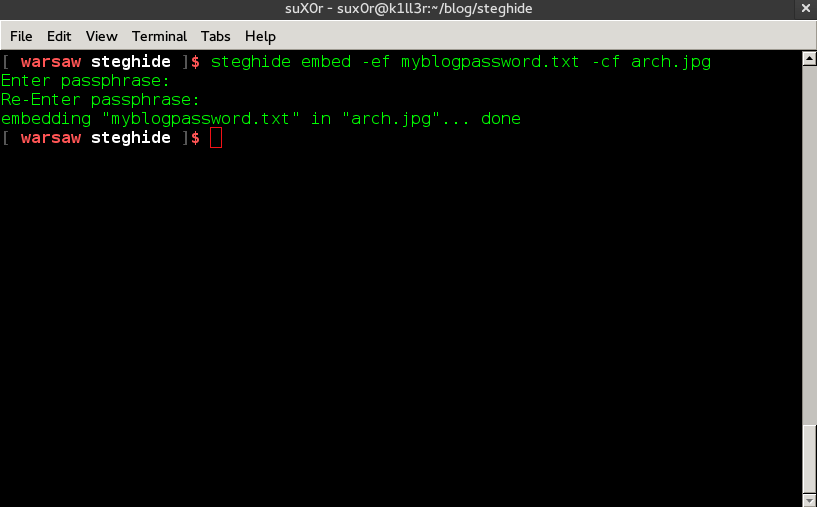
Now say I have a file with the name of myblogpassword.txt which contains the login password of my blog and I want to encode that file into an Image file with the name of arch.jpg so that I can hide my sensitive information from the preying eyes of my friends. In order to do that I'll type the following command in my terminal:
steghide embed -ef myblogpassword.txt -cf arch.jpg
here steghide is the name of the program
embed flag is used to specify to steghide that we want to embed one file into another file
-ef option is used to specify to steghide the name (and location, in case if its in some other directory) of the file that we want to embed inside of the another file, in our case its myblogpassword.txt
-cf option is used to specify the name (and location, in case if its in some other directory) of the file in which we want to embed our file, in our case its an image file named arch.jpg
After typing the above command and hitting enter it will prompt for a password. We can specify a password here in order to password protect our file so that when anyone tries to extract our embedded file, they'll have to supply a password in order to extract it. If you don't want to password protect it you can just simply hit enter.
Now myblogpassword.txt file is embedded inside of the image file arch.jpg. You'll see no changes in the image file except for its size. Now we can delete the plain password text file myblogpassword.txt.
In order to extract the embedded file from the cover file, I'll type following command in the terminal:
steghide extract -sf arch.jpg -xf myblogpass.txt
here steghide is again name of the program
extract flag specifies that we want to extract an embedded file from a stego file
-sf option specifies the name of the stego file or in other words the file in which we embedded another file, in our case here its the arch.jpg file
-xf option specifies the name of the file to which we want to write our embedded file, here it is myblogpass.txt
(remember you must specify the name of file with its location if its somewhere else than the current directory)
After typing the above command and hitting enter, it will prompt for a password. Supply the password if any or otherwise just simply hit enter. It will extract the embedded file to the file named myblogpass.txt. Voila! you got your file back but yes the image file still contains the embedded file.
That's it, very easy isn't it?
It was a pretty basic introduction you can look for other things like encrypting the file to be embedded before you embed it into another file and so on... enjoy :)
More info
2020. június 9., kedd
Practical Dictionary Attack On IPsec IKE
We found out that in contrast to public knowledge, the Pre-Shared Key (PSK) authentication method in main mode of IKEv1 is susceptible to offline dictionary attacks. This requires only a single active Man-in-the-Middle attack. Thus, if low entropy passwords are used as PSKs, this can easily be broken.
This week at the USENIX Security conference, Dennis Felsch will present our research paper on IPsec attacks: The Dangers of Key Reuse: Practical Attacks on IPsec IKE. [alternative link to the paper]
In his blog post, Dennis showed how to attack the public key encryption based authentication methods of IKEv1 (PKE & RPKE) and how to use this attack against IKEv2 signature based authentication method. In this blog post, I will focus on another interesting finding regarding IKEv1 and the Pre-Shared Key authentication.
IPsec and Internet Key Exchange (IKE)
IPsec enables cryptographic protection of IP packets. It is commonly used to build VPNs (Virtual Private Networks). For key establishment, the IKE protocol is used. IKE exists in two versions, each with different modes, different phases, several authentication methods, and configuration options. Therefore, IKE is one of the most complex cryptographic protocols in use.
In version 1 of IKE (IKEv1), four authentication methods are available for Phase 1, in which initial authenticated keying material is established: Two public key encryption based methods, one signature based method, and a PSK (Pre-Shared Key) based method.
Pre-Shared Key authentication
As shown above, Pre-Shared Key authentication is one of three authentication methods in IKEv1. The authentication is based on the knowledge of a shared secret string. In reality, this is probably some sort of password.
The IKEv1 handshake for PSK authentication looks like the following (simplified version):
In the first two messages, the session identifier (inside HDR) and the cryptographic algorithms (proposals) are selected by initiator and responder.
In messages 3 and 4, they exchange ephemeral Diffie-Hellman shares and nonces. After that, they compute a key k by using their shared secret (PSK) in a PRF function (e.g. HMAC-SHA1) and the previously exchanged nonces. This key is used to derive additional keys (ka, kd, ke). The key kd is used to compute MACI over the session identifier and the shared diffie-hellman secret gxy. Finally, the key ke is used to encrypt IDI (e.g. IPv4 address of the peer) and MACI.
Weaknesses of PSK authentication
It is well known that the aggressive mode of authentication in combination with PSK is insecure and vulnerable against off-line dictionary attacks, by simply eavesedropping the packets. For example, in strongSwan it is necessary to set the following configuration flag in order to use it:
charon.i_dont_care_about_security_and_use_aggressive_mode_psk=yes
For the main mode, we found a similar attack when doing some minor additional work. For that, the attacker needs to waits until a peer A (initiator) tries to connect to another peer B (responder). Then, the attacker acts as a man-in-the middle and behaves like the peer B would, but does not forward the packets to B.
From the picture above it should be clear that an attacker who acts as B can compute (gxy) and receives the necessary public values session ID, nI, nR. However, the attacker does not know the PSK. In order to mount a dictionary attack against this value, he uses the nonces, and computes a candidate for k for every entry in the dictionary. It is necessary to make a key derivation for every k with the values of the session identifiers and shared Diffie-Hellmann secret the possible keys ka, kd and ke. Then, the attacker uses ke in order to decrypt the encrypted part of message 5. Due to IDI often being an IP address plus some additional data of the initiator, the attacker can easily determine if the correct PSK has been found.
Who is affected?
This weakness exists in the IKEv1 standard (RFC 2409). Every software or hardware that is compliant to this standard is affected. Therefore, we encourage all vendors, companies, and developers to at least ensure that high-entropy Pre-Shared Keys are used in IKEv1 configurations.
In order to verify the attack, we tested the attack against strongSWAN 5.5.1.
Proof-of-Concept
We have implemented a PoC that runs a dictionary attack against a network capture (pcapng) of a IKEv1 main mode session. As input, it also requires the Diffie-Hellmann secret as described above. You can find the source code at github. We only tested the attack against strongSWAN 5.5.1. If you want to use the PoC against another implementation or session, you have to adjust the idHex value in main.py.
Responsible Disclosure
We reported our findings to the international CERT at July 6th, 2018. We were informed that they contacted over 250 parties about the weakness. The CVE ID for it is CVE-2018-5389 [cert entry].
Credits
On August 10th, 2018, we learned that this attack against IKEv1 main mode with PSKs was previously described by David McGrew in his blog post Great Cipher, But Where Did You Get That Key?. We would like to point out that neither we nor the USENIX reviewers nor the CERT were obviously aware of this.
On August 14th 2018, Graham Bartlett (Cisco) email us that he presented the weakness of PSK in IKEv2 in several public presentations and in his book.
On August 15th 2018, we were informed by Tamir Zegman that John Pliam described the attack on his web page in 1999.
On August 14th 2018, Graham Bartlett (Cisco) email us that he presented the weakness of PSK in IKEv2 in several public presentations and in his book.
On August 15th 2018, we were informed by Tamir Zegman that John Pliam described the attack on his web page in 1999.
FAQs
- Do you have a name, logo, any merchandising for the attack?
No. - Have I been attacked?
We mentioned above that such an attack would require an active man-in-the-middle attack. In the logs this could look like a failed connection attempt or a session timed out. But this is a rather weak indication and no evidence for an attack. - What should I do?
If you do not have the option to switch to authentication with digital signatures, choose a Pre-Shared Key that resists dictionary attacks. If you want to achieve e.g. 128 bits of security, configure a PSK with at least 19 random ASCII characters. And do not use something that can be found in public databases. - Am I safe if I use PSKs with IKEv2?
No, interestingly the standard also mentions that IKEv2 does not prevent against off-line dictionary attacks. - Where can I learn more?
You can read the paper. [alternative link to the paper] - What else does the paper contain?
The paper contains a lot more details than this blogpost. It explains all authentication methods of IKEv1 and it gives message flow diagrams of the protocol. There, we describe a variant of the attack that uses the Bleichenbacher oracles to forge signatures to target IKEv2.
Related posts
Part I. Russian APT - APT28 Collection Of Samples Including OSX XAgent
The post contains malware samples analyzed in the APT28 reports linked below. I will post APT29 and others later.
List of References (and samples mentioned) listed from oldest to newest:
- APT28_2011-09_Telus_Trojan.Win32.Sofacy.A
- APT28_2014-08_MhtMS12-27_Prevenity
- APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations
- APT28_2014-10_Telus_Coreshell.A
- APT28_2014-10_TrendMicro Operation Pawn Storm. Using Decoys to Evade Detection
- APT28_2015-07_Digital Attack on German Parliament
- APT28_2015-07_ESET_Sednit_meet_Hacking
- APT28_2015-07_Telus_Trojan-Downloader.Win32.Sofacy.B
- APT28_2015-09_Root9_APT28_Technical_Followup
- APT28_2015-09_SFecure_Sofacy-recycles-carberp-and-metasploit-code
- APT28_2015-10_New Adobe Flash Zero-Day Used in Pawn Storm
- APT28_2015-10_Root9_APT28_targets Financial Markets
- APT28_2015-12_Bitdefender_In-depth_analysis_of_APT28–The_Political_Cyber-Espionage
- APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets
- APT28_2015_06_Microsoft_Security_Intelligence_Report_V19
- APT28_2016-02_PaloAlto_Fysbis Sofacy Linux Backdoor
- APT29_2016-06_Crowdstrike_Bears in the Midst Intrusion into the Democratic National Committee << DNC (NOTE: this is APT29)
- APT28_2016-07_Invincea_Tunnel of Gov DNC Hack and the Russian XTunnel
- APT28_2016-10_ESET_Observing the Comings and Goings
- APT28_2016-10_ESET_Sednit A Mysterious Downloader
- APT28_2016-10_ESET_Sednit Approaching the Target
- APT28_2016-10_Sekoia_Rootkit analysisUse case on HideDRV
- APT28_2017-02_Bitdefender_OSX_XAgent << OSX XAgent
Download
 Download sets (matching research listed above). Email me if you need the password
Download sets (matching research listed above). Email me if you need the passwordDownload all files/folders listed (72MB)
| Parent Folder | File Name (SHA1) | MD5 Checksum | SHA256 Checksum |
|---|---|---|---|
| APT28 | APT28_2011-09_Telus_Trojan.Win32.Sofacy.A | ||
| APT28_2011-09_Telus_Trojan.Win32.Sofacy.A | 28F21E96E0722DD6FC7D6E1275F352BD060ADE0D | 1e217668d89b480ad42e230e8c2c4d97 | 1feb41c4a64a7588d1e8e02497627654e9d031e7020d010541d8a8626447dbe9 |
| APT28_2011-09_Telus_Trojan.Win32.Sofacy.A | 72CFD996957BDE06A02B0ADB2D66D8AA9C25BF37 | ed7f6260dec470e81dafb0e63bafb5ae | 7313eaf95a8a8b4c206b9afe306e7c0675a21999921a71a5a16456894571d21d |
| APT28_2011-09_Telus_Trojan.Win32.Sofacy.A | AC6B465A13370F87CF57929B7CFD1E45C3694585 | e1554b931affb3cd2edc90bc58028078 | 5ab8ef93fdeaac9af258845ab52c24d31140c8fffc5fdcf465529c8e00c508ac |
| APT28_2011-09_Telus_Trojan.Win32.Sofacy.A | C01B02CCC86ACBD9B266B09D2B693CB39A2C6809 | 9e4817f7bf36a61b363e0911cc0f08b9 | 31a0906b0d8b07167129e134009dc307c2d92522da5709e52b67d3c5a70adf93 |
| APT28 | APT28_2014-08_MhtMS12-27_Prevenity | ||
| APT28_2014-08_MhtMS12-27_Prevenity | 33EEC0D1AE550FB33874EDCE0138F485538BB21B__.mht_ | d3de5b8500453107d6d152b3c8506935 | 55038c4326964f480fd2160b6b2a7aff9e980270d7765418937b3daeb4e82814 |
| APT28_2014-08_MhtMS12-27_Prevenity | 8DEF0A554F19134A5DB3D2AE949F9500CE3DD2CE_filee.dll_ | 16a6c56ba458ec718b4e9bc8f9f10785 | ce554d57333bdbccebb5e2e8d16a304947981e48ea2a5cc3d5f4ced7c1f56df3 |
| APT28_2014-08_MhtMS12-27_Prevenity | A8551397E1F1A2C0148E6EADCB56FA35EE6009CA_coreshell.dll_ | 48656a93f9ba39410763a2196aabc67f | c8087186a215553d2f95c68c03398e17e67517553f6e9a8adc906faa51bce946 |
| APT28_2014-08_MhtMS12-27_Prevenity | E338A57C35A4732BBB5F738E2387C1671A002BCB_advstorshell.dll_ | d7a625779df56d874871bb632f3e3106 | 11097a7a3336e0ab124fa921b94e3d51c4e9e4424e140e96127bfcf1c10ef110 |
| APT28 | APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | ||
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | 367D40465FD1633C435B966FA9B289188AA444BC__tmp64.dat_ | 791428601ad12b9230b9ace4f2138713 | 29cc2e69f65b9ce5fe04eb9b65942b2dabf48e41770f0a49eb698271b99d2787 |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | 6316258CA5BA2D85134AD7427F24A8A51CE4815B_coreshell.dll_ | da2a657dc69d7320f2ffc87013f257ad | d54173be095b688016528f18dc97f2d583efcf5ce562ec766afc0b294eb51ac7 |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | 682E49EFA6D2549147A21993D64291BFA40D815A_coreshell.dll_ | 3b0ecd011500f61237c205834db0e13a | 7f6f9645499f5840b59fb59525343045abf91bc57183aae459dca98dc8216965 |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | 85522190958C82589FA290C0835805F3D9A2F8D6_coreshell.dll_ | 8b92fe86c5b7a9e34f433a6fbac8bc3a | 03ed773bde6c6a1ac3b24bde6003322df8d41d3d1c85109b8669c430b58d2f69 |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | A8551397E1F1A2C0148E6EADCB56FA35EE6009CA_coreshell.dll_ | 48656a93f9ba39410763a2196aabc67f | c8087186a215553d2f95c68c03398e17e67517553f6e9a8adc906faa51bce946 |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | CF3220C867B81949D1CE2B36446642DE7894C6DC_coreshell.dll_ | 5882fda97fdf78b47081cc4105d44f7c | 744f2a1e1a62dff2a8d5bd273304a4d21ee37a3c9b0bdcffeeca50374bd10a39 |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | D87B310AA81AE6254FFF27B7D57F76035F544073_coreshell.dll_ | 272f0fde35dbdfccbca1e33373b3570d | 423a0799efe41b28a8b765fa505699183c8278d5a7bf07658b3bd507bfa5346f |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | D9C53ADCE8C35EC3B1E015EC8011078902E6800B_coreshell.dll_ | 1259c4fe5efd9bf07fc4c78466f2dd09 | 102b0158bcd5a8b64de44d9f765193dd80df1504e398ce52d37b7c8c33f2552a |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | E2450DFFA675C61AA43077B25B12851A910EEEB6_ coreshell.dll_ | 9eebfebe3987fec3c395594dc57a0c4c | e6d09ce32cc62b6f17279204fac1771a6eb35077bb79471115e8dfed2c86cd75 |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | ED48EF531D96E8C7360701DA1C57E2FF13F12405_coreshell.dll_ | ead4ec18ebce6890d20757bb9f5285b1 | 7695f20315f84bb1d940149b17dd58383210ea3498450b45fefa22a450e79683 |
| APT28_2014-10_Fireeye_A_Window_into_Russia_Cyber_Esp.Operations | F5B3E98C6B5D65807DA66D50BD5730D35692174D_asdfasdf.dat_ | 8c4fa713c5e2b009114adda758adc445 | d58f2a799552aff8358e9c63a4345ea971b27edd14b8eac825db30a8321d1a7a |
| APT28 | APT28_2014-10_Telus_Coreshell.A | ||
| APT28_2014-10_Telus_Coreshell.A | D87B310AA81AE6254FFF27B7D57F76035F544073_coreshell.dll_ | 272f0fde35dbdfccbca1e33373b3570d | 423a0799efe41b28a8b765fa505699183c8278d5a7bf07658b3bd507bfa5346f |
| APT28 | APT28_2014-10_TrendMicro Operation Pawn Storm | ||
| APT28_2014-10_TrendMicro Operation Pawn Storm | 0A3E6607D5E9C59C712106C355962B11DA2902FC_Case2_S.vbs_exe_ | db9edafbadd71c7a3a0f0aec1b216a92 | b3d624c4287795a7fbddd617f57705153d30f5f4c4d2d1fec349ac2812c3a8a0 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 0E12C8AB9B89B6EB6BAF16C4B3BBF9530067963F_Case2_Military CooperationDecoy.doc_ | 7fcf20302404f644fb07fe9d4fe9ac84 | 77166146463b9124e075f3a7925075f969974e32746c78d022ba99f578b9f0bb |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 14BEEB0FC5C8C887D0435009730B6370BF94BC93_Case5Payload2_netids.dll_ | 35717cd78ce713067a5037286cf91c3e | 1b3dd8aaafd750aa85185dc52672b26d67d662796847d7cbb01a35b565e74d35 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 3814EEC8C45FC4313A9C7F65CE882A7899CF0405_Case4_NetIds.dll_ | a24552843b9fedd7d0084e1eb1dd6e35 | 966660738c9e3ec103c2f8fe361c8ac20647cacaa5153197fa1917e9da99082e |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 4B8806FE8E0CB49E4AA5D8F87766415A2DB1E9A9_Case2dropper_cryptmodule.exe_ | 41e14894f4ad9494e0359ee5bb3d9745 | 684f4b9ea61e14a15e82cac25076c5afe2d30e3dad7ce0b1b375b24d81135c37 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 550ABD71650BAEA05A0071C4E084A803CB413C31_Case2_skype.exe_ | 7276d1dab1125f59604252159e0c529c | 81f0f5fcb3cb8a63e8a3713b4107b89d888cb722cb6c7586c7fcdb45f5310174 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 55318328511961EC339DFDDCA0443068DCCE9CD2_Case3_conhost.dll_ | f1704aaf08cd66a2ac6cf8810c9e07c2 | 74bdd9c250b0f4f27c0ecfeca967f53b35265c785d67406cc5e981a807d741bd |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 5A452E7248A8D3745EF53CF2B1F3D7D8479546B9_Case3_netui.dll_keylog | aa3e6af90c144112a1ad0c19bdf873ff | 4536650c9c5e5e1bb57d9bedf7f9a543d6f09addf857f0d802fb64e437b6844a |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 6ADA11C71A5176A82A8898680ED1EAA4E79B9BC3_Case1_Letter to IAEA.pdf_decoy | 76d3eb8c2bed4f2588e22b8d0984af86 | b0f1f553a847f3244f434541edbf26904e2de18cca8db8f861ea33bb70942b61 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 6B875661A74C4673AE6EE89ACC5CB6927CA5FD0D_Case2Payload2_ netids.dll_ | 42bc93c0caddf07fce919d126a6e378f | 9392776d6d8e697468ab671b43dce2b7baf97057b53bd3517ecd77a081eff67d |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 72CFD996957BDE06A02B0ADB2D66D8AA9C25BF37_Case1_saver.scr_ | ed7f6260dec470e81dafb0e63bafb5ae | 7313eaf95a8a8b4c206b9afe306e7c0675a21999921a71a5a16456894571d21d |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 78D28072FDABF0B5AAC5E8F337DC768D07B63E1E_Case5_IDF_Spokesperson_Terror_Attack_011012.doc_ | 1ac15db72e6d4440f0b4f710a516b165 | 0cccb9d951ba888c0c37bb0977fbb3682c09f9df1b537eede5a1601e744a01ad |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 7FBB5A2E46FACD3EE0C945F324414210C2199FFB_Case5payload_saver.scr_ | c16b07f7590a8620a8f0f687b0bd8bd8 | cb630234494f2424d8e158c6471f0b6d0643abbdf2f3e378bc2f68c9e7bca9eb |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 88F7E271E54C127912DB4DB49E37D93AEA8A49C9_Case3_download_msmvs.exe_ | 66f368cab3d5e64475a91f636c87af15 | e8ac9acc6fa3283276bbb77cff2b54d963066659b65e48cd8803a2007839af25 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 8DEF0A554F19134A5DB3D2AE949F9500CE3DD2CE_Case6_dropper_filee.dll_ | 16a6c56ba458ec718b4e9bc8f9f10785 | ce554d57333bdbccebb5e2e8d16a304947981e48ea2a5cc3d5f4ced7c1f56df3 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 956D1A36055C903CB570890DA69DEABAACB5A18A_Case2_International Military.rtf_ | d994b9780b69f611284e22033e435edb | 342e1f591ab45fcca6cee7f5da118a99dce463e222c03511c3f1288ac2cf82c8 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | 9C622B39521183DD71ED2A174031CA159BEB6479_Case3_conhost.dll__ | d4e99548832b6999f00e8d223c6fabbd | d5debe5d88e76a409b9bc3f69a02a7497d333934d66f6aaa30eb22e45b81a9ab |
| APT28_2014-10_TrendMicro Operation Pawn Storm | A8551397E1F1A2C0148E6EADCB56FA35EE6009CA_Case6_Coreshell.dll_ | 48656a93f9ba39410763a2196aabc67f | c8087186a215553d2f95c68c03398e17e67517553f6e9a8adc906faa51bce946 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | A90921C182CB90807102EF402719EE8060910345_Case4_APEC Media list 2013 Part1.xls_ | aeebfc9eb9031e423797a5af1985242d | e8d3f1e4e0d7c19e195d92be5cb6b3617a0496554c892e93b66a75c411745c05 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | AC6B465A13370F87CF57929B7CFD1E45C3694585_Case4Payload_dw20.t_ | e1554b931affb3cd2edc90bc58028078 | 5ab8ef93fdeaac9af258845ab52c24d31140c8fffc5fdcf465529c8e00c508ac |
| APT28_2014-10_TrendMicro Operation Pawn Storm | B3098F99DB1F80E27AEC0C9A5A625AEDAAB5899A_APEC Media list 2013 Part2.xls_decoy | bebb3675cfa4adaba7822cc8c39f55bf | 8fc4fe966ef4e7ecf635283a6fa6bacd8586ee8f0d4d39c6faffd49d60b01cb9 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | BC58A8550C53689C8148B021C917FB4AEEC62AC1_Case5Payload_install.exe_ | c43edb579e43aaeb6f0c0703f84e43f7 | 7dd063acdfb00509b3b06718b39ae53e2ff2fc080094145ce138abb1f2253de4 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | C5CE5B7D10ACCB04A4E45C3A4DCF10D16B192E2F_Case1Payload_netids.dll_ | 85c80d01661f88ec556579e772a5a3db | 461f5340f9ea47344f86bb7302fbaaa0567605134ec880eef34fa9b40926eb70 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | D0AA4F3229FCD9A57E9E4F08860F3CC48C983ADDml.rtf | a24d2f5258f8a0c3bddd1b5636b0ec57 | 992caa9e8de503fb304f97d1ab0b92202d2efb0d1353d19ce7bec512faf76491 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | DAE7FAA1725DB8192AD711D759B13F8195A18821_Case6_MH17.doc_decoy | 388594cd1bef96121be291880b22041a | adf344f12633ab0738d25e38f40c6adc9199467838ec14428413b1264b1bf540 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | E338A57C35A4732BBB5F738E2387C1671A002BCB_Case6_advstoreshell.dll_ | d7a625779df56d874871bb632f3e3106 | 11097a7a3336e0ab124fa921b94e3d51c4e9e4424e140e96127bfcf1c10ef110 |
| APT28_2014-10_TrendMicro Operation Pawn Storm | F542C5F9259274D94360013D14FFBECC43AAE552_Case5Decoy_IDF_Spokesperson_Terror_Attack_011012.doc_ | 77aa465744061b4b725f73848aebdff6 | 91f750f422fd3ff361fabca02901830ef3f6e5829f6e8db9c1f518a1a3cac08c |
| APT28_2014-10_TrendMicro Operation Pawn Storm | wp-operation-pawn-storm.pdf | ce254486b02be740488c0ab3278956fd | 9b8495ff1d023e3ae7aed799f02d9cf24422a38dfb9ed37c0bdc65da55b4ee42 |
| APT28 | APT28_2015-07_Digital Attack on German Parliament | ||
| APT28_2015-07_Digital Attack on German Parliament | 0450AAF8ED309CA6BAF303837701B5B23AAC6F05_servicehost.dll_ | 800af1c9d341b846a856a1e686be6a3e | 566ab945f61be016bfd9e83cc1b64f783b9b8deb891e6d504d3442bc8281b092 |
| APT28_2015-07_Digital Attack on German Parliament | CDEEA936331FCDD8158C876E9D23539F8976C305_exe_ | 5e70a5c47c6b59dae7faf0f2d62b28b3 | 730a0e3daf0b54f065bdd2ca427fbe10e8d4e28646a5dc40cbcfb15e1702ed9a |
| APT28_2015-07_Digital Attack on German Parliament | Digital Attack on German Parliament_ Investigative Report on the Hack of the Left Party Infrastructure in Bundestag _ netzpolitik.pdf | 28d4cc2a378633e0ad6f3306cc067c43 | e83e2185f9e1a5dbc550914dcbc7a4d0f8b30a577ddb4cd8a0f36ac024a68aa0 |
| APT28_2015-07_Digital Attack on German Parliament | F46F84E53263A33E266AAE520CB2C1BD0A73354E_winexesvc.exe_ | 77e7fb6b56c3ece4ef4e93b6dc608be0 | 5130f600cd9a9cdc82d4bad938b20cbd2f699aadb76e7f3f1a93602330d9997d |
| APT28 | APT28_2015-07_ESET_Sednit_meet_Hacking | ||
| APT28_2015-07_ESET_Sednit_meet_Hacking | 51B0E3CD6360D50424BF776B3CD673DD45FD0F97.exe_ | 973e0c922eb07aad530d8a1de19c7755 | 7c4101caf833aa9025fec4f04a637c049c929459ad3e4023ba27ac72bde7638d |
| APT28_2015-07_ESET_Sednit_meet_Hacking | B8B3F53CA2CD64BD101CB59C6553F6289A72D9BBdll_ | dcf6906a9a0c970bcd93f451b9b7932a | 9a527274f99865a7d70487fe22e62f692f8b239d6cb80816b919734c7c741584 |
| APT28_2015-07_ESET_Sednit_meet_Hacking | D43FD6579AB8B9C40524CC8E4B7BD05BE6674F6C_warfsgfdydcikf.mkv.swf_ | 557f8d4c6f8b386c32001def807dc715 | 84ad945d1ab58591efb21b863320f533c53b2398a1bc690d221e1c1c77fa27ff |
| APT28 | APT28_2015-07_Telus_Trojan-Downloader.Win32.Sofacy.B | ||
| APT28_2015-07_Telus_Trojan-Downloader.Win32.Sofacy.B | B8B3F53CA2CD64BD101CB59C6553F6289A72D9BB.dll_ | dcf6906a9a0c970bcd93f451b9b7932a | 9a527274f99865a7d70487fe22e62f692f8b239d6cb80816b919734c7c741584 |
| APT28 | APT28_2015-09_Root9_APT28_Technical_Followup | ||
| APT28_2015-09_Root9_APT28_Technical_Followup | 0450AAF8ED309CA6BAF303837701B5B23AAC6F05_servicehost.dll_ | 800af1c9d341b846a856a1e686be6a3e | 566ab945f61be016bfd9e83cc1b64f783b9b8deb891e6d504d3442bc8281b092 |
| APT28_2015-09_Root9_APT28_Technical_Followup | CDEEA936331FCDD8158C876E9D23539F8976C305_exe_ | 5e70a5c47c6b59dae7faf0f2d62b28b3 | 730a0e3daf0b54f065bdd2ca427fbe10e8d4e28646a5dc40cbcfb15e1702ed9a |
| APT28_2015-09_Root9_APT28_Technical_Followup | F46F84E53263A33E266AAE520CB2C1BD0A73354E_winexesvc.exe_ | 77e7fb6b56c3ece4ef4e93b6dc608be0 | 5130f600cd9a9cdc82d4bad938b20cbd2f699aadb76e7f3f1a93602330d9997d |
| APT28 | APT28_2015-09_SFecure_Sofacy-recycles-carberp-and-metasploit-code | ||
| APT28_2015-09_SFecure_Sofacy-recycles-carberp-and-metasploit-code | Dlls | ||
| Dlls | 21835AAFE6D46840BB697E8B0D4AAC06DEC44F5B | 211b7100fd799e9eaabeb13cfa446231 | 3d13f2e5b241168005425b15410556bcf26d04078da6b2ef42bc0c2be7654bf8 |
| Dlls | 3B52046DD7E1D5684EABBD9038B651726714AB69 | d535c3fc5f0f98e021bea0d6277d2559 | d4525abc9dd2b7ab7f0c22e58a0117980039afdf15bed04bb0c637cd41fbfb9d |
| Dlls | 5C3E709517F41FEBF03109FA9D597F2CCC495956 | ac75fd7d79e64384b9c4053b37e5623f | 0ac7b666814fd016b3d21d7812f4a272104511f90ca666fa13e9fb6cefa603c7 |
| Dlls | 7319A2751BD13B2364031F1E69035ACFC4FD4D18 | c0d1762561f8c2f812d868a3939d23f0 | 8325cd6e26fb39cf7a08787e771a6cf708e0b45350d1ea239982af06db90804f |
| Dlls | 9FC43E32C887B7697BF6D6933E9859D29581EAD0 | a3c757af9e7a9a60e235d08d54740fbc | bf28267386a010197a50b65f24e815aa527f2adbc53c609d2b2a4f999a639413 |
| Dlls | AC61A299F81D1CFF4EA857AFD1B323724AAC3F04 | acf8cda38b0d1b6a0d3664a0e33deb96 | 638e7ca68643d4b01432f0ecaaa0495b805cc3cccc17a753b0fa511d94a22bdd |
| Dlls | B8B3F53CA2CD64BD101CB59C6553F6289A72D9BB | dcf6906a9a0c970bcd93f451b9b7932a | 9a527274f99865a7d70487fe22e62f692f8b239d6cb80816b919734c7c741584 |
| Dlls | D3AA282B390A5CB29D15A97E0A046305038DBEFE | 18efc091b431c39d3e59be445429a7bc | eae782130b06d95f3373ff7d5c0977a8019960bdf80614c1aa7e324dc350428a |
| Dlls | D85E44D386315B0258847495BE1711450AC02D9F | c4ffab85d84b494e1c450819a0e9c7db | 500fa112a204b6abb365101013a17749ce83403c30cd37f7c6f94e693c2d492f |
| Dlls | ED9F3E5E889D281437B945993C6C2A80C60FDEDC | 2dfc90375a09459033d430d046216d22 | 261b0a5912965ea95b8ae02aae1e761a61f9ad3a9fb85ef781e62013d6a21368 |
| Dlls | F7608EF62A45822E9300D390064E667028B75DEA | 75f71713a429589e87cf2656107d2bfc | b6fff95a74f9847f1a4282b38f148d80e4684d9c35d9ae79fad813d5dc0fd7a9 |
| APT28_2015-09_SFecure_Sofacy-recycles-carberp-and-metasploit-code | Droppers | ||
| Droppers | 015425010BD4CF9D511F7FCD0FC17FC17C23EEC1 | c2a0344a2bbb29d9b56d378386afcbed | 63d0b28114f6277b901132bc1cc1f541a594ee72f27d95653c54e1b73382a5f6 |
| Droppers | 4FAE67D3988DA117608A7548D9029CADDBFB3EBF | c6a80316ea97218df11e11125337233a | b0b3f0d6e6c593e2a2046833080574f98566c48a1eda865b2e110cd41bf31a31 |
| Droppers | 51B0E3CD6360D50424BF776B3CD673DD45FD0F97 | 973e0c922eb07aad530d8a1de19c7755 | 7c4101caf833aa9025fec4f04a637c049c929459ad3e4023ba27ac72bde7638d |
| Droppers | 63D1D33E7418DAF200DC4660FC9A59492DDD50D9 | 2d4eaa0331abbc6d867f5f979b2c890d | b4f755c91c2790f4ab9bac4ee60725132323e13a2688f3d8939ae9ed4793d014 |
| Droppers | B4A515EF9DE037F18D96B9B0E48271180F5725B7 | afe09fb5a2b97f9e119f70292092604e | d93f22d46090bfc19ef51963a781eeb864390c66d9347e86e03bba25a1fc29c5 |
| Droppers | B7788AF2EF073D7B3FB84086496896E7404E625E | eda061c497ba73441994a30e36f55b1d | b1800cb1d4b755e05b0fca251b8c6da96bb85f8042f2d755b7f607cbeef58db8 |
| Droppers | B8AABE12502F7D55AE332905ACEE80A10E3BC399 | 91381cd82cdd5f52bbc7b30d34cb8d83 | 1a09ce8a9210d2530d6ce1d59bfae2ac617ac89558cdcdcac15392d176e70c8d |
| Droppers | F3D50C1F7D5F322C1A1F9A72FF122CAC990881EE | 77089c094c0f2c15898ff0f021945148 | eb6620442c3ab327f3ccff1cc6d63d6ffe7729186f7e8ac1dbbbfddd971528f0 |
| APT28 | APT28_2015-10_New Adobe Flash Zero-Day Used in Pawn Storm | ||
| APT28_2015-10_New Adobe Flash Zero-Day Used in Pawn Storm | 2DF498F32D8BAD89D0D6D30275C19127763D5568763D5568.swf_ | 6ca857721be6fff26b10867c99bd8c80 | b4064721d911e9606edf366173325945f9e940e489101e7d0747103c0e905126 |
| APT28_2015-10_New Adobe Flash Zero-Day Used in Pawn Storm | A5FCA59A2FAE0A12512336CA1B78F857AFC06445AFC06445_ mgswizap.dll_ | f1d3447a2bff56646478b0adb7d0451c | 5a414a39851c4e22d4f9383211dfc080e16e2caffd90fa06dcbe51d11fdb0d6c |
| APT28 | APT28_2015-10_Root9_APT28_targets Financial Markets | ||
| APT28_2015-10_Root9_APT28_targets Financial Markets | 0450AAF8ED309CA6BAF303837701B5B23AAC6F05_servicehost.dll_ | 800af1c9d341b846a856a1e686be6a3e | 566ab945f61be016bfd9e83cc1b64f783b9b8deb891e6d504d3442bc8281b092 |
| APT28_2015-10_Root9_APT28_targets Financial Markets | F325970FD24BB088F1BEFDAE5788152329E26BF3_SupUpNvidia.exe_ | 0369620eb139c3875a62e36bb7abdae8 | b1f2d461856bb6f2760785ee1af1a33c71f84986edf7322d3e9bd974ca95f92d |
| APT28 | APT28_2015-12_Bitdefender_In-depth_analysis_of_APT28â€"The_Political_Cyber-Espionage | ||
| APT28_2015-12_Bitdefender_In-depth_analysis_of_APT28â€"The_Political_Cyber-Espionage | Bitdefender_In-depth_analysis_of_APT28â€"The_Political_Cyber-Espionage.pdf | 1a5d89f6fd3f1ed5f4e76084b0fa7806 | a76b1ec9d196b5c071992486d096ad475226e92b6db06c351e3a4ad4e4949248 |
| APT28_2015-12_Bitdefender_In-depth_analysis_of_APT28â€"The_Political_Cyber-Espionage | CB796F2986700DF9CE7D8F8D7A3F47F2EB4DF682_xp.exe_APT28 | 78450806e56b1f224d00455efcd04ce3 | b29a16ec907997e523f97e77b885d4a8c19cb81b1abf6ee51eee54f37eecf3ff |
| APT28_2015-12_Bitdefender_In-depth_analysis_of_APT28â€"The_Political_Cyber-Espionage | F080E509C988A9578862665B4FCF1E4BF8D77C3E_Linux.Fysbis.A_ksysdefd_elf_APT28 | 075b6695ab63f36af65f7ffd45cccd39 | 02c7cf55fd5c5809ce2dce56085ba43795f2480423a4256537bfdfda0df85592 |
| APT28_2015-12_Bitdefender_In-depth_analysis_of_APT28â€"The_Political_Cyber-Espionage | SIMILAR | ||
| SIMILAR | 356d03f6975f443d6db6c5069d778af9_exe_ | 356d03f6975f443d6db6c5069d778af9 | 3f14fc9c29763da76dcbc8a2aaa61658781d1b215ee322a0ebfa554d8658d22b |
| SIMILAR | 78450806e56b1f224d00455efcd04ce3_xp.exe_APT28 | 78450806e56b1f224d00455efcd04ce3 | b29a16ec907997e523f97e77b885d4a8c19cb81b1abf6ee51eee54f37eecf3ff |
| SIMILAR | e49bce75070a7a3c63a7cebb699342b3_CVE-2014-4076_tan.exe_ | e49bce75070a7a3c63a7cebb699342b3 | 16d49a40333f584b19606733b4deef1b9ecace2c32950010ad1450b44ce3716e |
| APT28 | APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | ||
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | 1A4F39C0262822B0623213B8ED3F56DEE0117CD59_tf394kv.dll_ | 8c4d896957c36ec4abeb07b2802268b9 | 6cd30c85dd8a64ca529c6eab98a757fb326de639a39b597414d5340285ba91c6 |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | 1A4F39C0262822B0623213B8ED3F56DEE0117CD5_tf394kv.dll_ | 8c4d896957c36ec4abeb07b2802268b9 | 6cd30c85dd8a64ca529c6eab98a757fb326de639a39b597414d5340285ba91c6 |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | 314EF7909CA0ED3A744D2F59AB5AC8B8AE259319.dll_(4.3)AZZYimplants-USBStealer | f6f88caf49a3e32174387cacfa144a89 | e917166adf6e1135444f327d8fff6ec6c6a8606d65dda4e24c2f416d23b69d45 |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | 3E2E245B635B04F006A0044388BD968DF9C3238C_IGFSRVC.dll_USBStealer | ce151285e8f0e7b2b90162ba171a4b90 | 4e4606313c423b681e11110ca5ed3a2b2632ec6c556b7ab9642372ae709555f3 |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | 776C04A10BDEEC9C10F51632A589E2C52AABDF48_USBGuard.exe_ | 8cb08140ddb00ac373d29d37657a03cc | 690b483751b890d487bb63712e5e79fca3903a5623f22416db29a0193dc10527 |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | AF86743852CC9DF557B62485715AF4C6D73644D3_AZZY4.3installer | c3ae4a37094ecfe95c2badecf40bf5bb | 67ecc3b8c6057090c7982883e8d9d0389a8a8f6e8b00f9e9b73c45b008241322 |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | C78FCAE030A66F388BF8CEA569422F5A79B7B96C_tmpdt.tmp_(4.3)AZZYimplant | ce8b99df8642c065b6af43fde1f786a3 | 1bab1a3e0e501d3c14652ecf60870e483ed4e90e500987c35489f17a44fef26c |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | C78FCAE030A66F388BF8CEA569422F5A79B7B96C_tmpdt.tmp__ | ce8b99df8642c065b6af43fde1f786a3 | 1bab1a3e0e501d3c14652ecf60870e483ed4e90e500987c35489f17a44fef26c |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | E251B3EB1449F7016DF78D113571BEA57F92FC36c_servicehost.dll_USBStealer | 8b238931a7f64fddcad3057a96855f6c | 92dcb0d8394d0df1064e68d90cd90a6ae5863e91f194cbaac85ec21c202f581f |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | E3B7704D4C887B40A9802E0695BAE379358F3BA0_Stand-aloneAZZYbackdoor | a96f4b8ac7aa9dbf4624424b7602d4f7 | a9dc96d45702538c2086a749ba2fb467ba8d8b603e513bdef62a024dfeb124cb |
| APT28_2015-12_Kaspersky_Sofacy APT hits high profile targets | F325970FD24BB088F1BEFDAE5788152329E26BF3_SupUpNvidia.exe_USBStealer | 0369620eb139c3875a62e36bb7abdae8 | b1f2d461856bb6f2760785ee1af1a33c71f84986edf7322d3e9bd974ca95f92d |
| APT28 | APT28_2015_06_Microsoft_Security_Intelligence_Report_V19 | ||
| APT28_2015_06_Microsoft_Security_Intelligence_Report_V19 | 0450AAF8ED309CA6BAF303837701B5B23AAC6F05_servicehost.dll_ | 800af1c9d341b846a856a1e686be6a3e | 566ab945f61be016bfd9e83cc1b64f783b9b8deb891e6d504d3442bc8281b092 |
| APT28_2015_06_Microsoft_Security_Intelligence_Report_V19 | 1535D85BEE8A9ADB52E8179AF20983FB0558CCB3.exe_ | 4ac8d16ff796e825625ad1861546e2e8 | 8c488b029188e3280ed3614346575a4a390e0dda002bca08c0335210a6202949 |
| APT28 | APT28_2016-02_PaloAlto_Fysbis Sofacy Linux Backdoor | ||
| APT28_2016-02_PaloAlto_Fysbis Sofacy Linux Backdoor | 9444D2B29C6401BC7C2D14F071B11EC9014AE040_Fysbis_elf_ | 364ff454dcf00420cff13a57bcb78467 | 8bca0031f3b691421cb15f9c6e71ce193355d2d8cf2b190438b6962761d0c6bb |
| APT28_2016-02_PaloAlto_Fysbis Sofacy Linux Backdoor | A Look Into Fysbis_ Sofacy’s Linux Backdoor - Palo Alto Networks Blog.pdf | 9a6b771c934415f74a203e0dfab9edbe | 1b6c3e6ef673f14536ff8d7c2bf18f9358a9a7f8962a24e2255f54ac451af86c |
| APT28_2016-02_PaloAlto_Fysbis Sofacy Linux Backdoor | ECDDA7ACA5C805E5BE6E0AB2017592439DE7E32C_ksysdefd_elf | e107c5c84ded6cd9391aede7f04d64c8 | fd8b2ea9a2e8a67e4cb3904b49c789d57ed9b1ce5bebfe54fe3d98214d6a0f61 |
| APT28_2016-02_PaloAlto_Fysbis Sofacy Linux Backdoor | F080E509C988A9578862665B4FCF1E4BF8D77C3E | 075b6695ab63f36af65f7ffd45cccd39 | 02c7cf55fd5c5809ce2dce56085ba43795f2480423a4256537bfdfda0df85592 |
| APT29 | APT29_2016-06_Crowdstrike_Bears in the Midst Intrusion into the Democratic National Committee | ||
| APT29_2016-06_Crowdstrike_Bears in the Midst Intrusion into the Democratic National Committee | 0B3852AE641DF8ADA629E245747062F889B26659.exe_ | cc9e6578a47182a941a478b276320e06 | fd39d2837b30e7233bc54598ff51bdc2f8c418fa5b94dea2cadb24cf40f395e5 |
| APT29_2016-06_Crowdstrike_Bears in the Midst Intrusion into the Democratic National Committee | 74C190CD0C42304720C686D50F8184AC3FADDBE9.exe_ | 19172b9210295518ca52e93a29cfe8f4 | 40ae43b7d6c413becc92b07076fa128b875c8dbb4da7c036639eccf5a9fc784f |
| APT29_2016-06_Crowdstrike_Bears in the Midst Intrusion into the Democratic National Committee | Bears in the Midst_ Intrusion into the Democratic National Committee ».pdf | dd5e31f9d323e6c3e09e367e6bd0e7b1 | 2d815b11f3b916bdc27b049402f5f1c024cffe2318a4f27ebfa3b8a9fffe2880 |
| APT29_2016-06_Crowdstrike_Bears in the Midst Intrusion into the Democratic National Committee | CB872EDD1F532C10D0167C99530A65C4D4532A1E.exe_ | ce227ae503e166b77bf46b6c8f5ee4da | b101cd29e18a515753409ae86ce68a4cedbe0d640d385eb24b9bbb69cf8186ae |
| APT29_2016-06_Crowdstrike_Bears in the Midst Intrusion into the Democratic National Committee | E2B98C594961AAE731B0CCEE5F9607080EC57197_pagemgr.exe_ | 004b55a66b3a86a1ce0a0b9b69b95976 | 6c1bce76f4d2358656132b6b1d471571820688ccdbaca0d86d0ca082b9390536 |
| APT29_2016-06_Crowdstrike_Bears in the Midst Intrusion into the Democratic National Committee | F09780BA9EB7F7426F93126BC198292F5106424B_VmUpgradeHelper.exe_ | 9e7053a4b6c9081220a694ec93211b4e | 4845761c9bed0563d0aa83613311191e075a9b58861e80392914d61a21bad976 |
| APT28 | APT28_2016-07_Invincea_Tunnel of Gov DNC Hack and the Russian XTunnel | ||
| APT28_2016-07_Invincea_Tunnel of Gov DNC Hack and the Russian XTunnel | E2101519714F8A4056A9DE18443BC6E8A1F1B977_PortMapClient.exe_ | ad44a7c5e18e9958dda66ccfc406cd44 | b81b10bdf4f29347979ea8a1715cbfc560e3452ba9fffcc33cd19a3dc47083a4 |
| APT28_2016-07_Invincea_Tunnel of Gov DNC Hack and the Russian XTunnel | F09780BA9EB7F7426F93126BC198292F5106424B_VmUpgradeHelper.exe_ | 9e7053a4b6c9081220a694ec93211b4e | 4845761c9bed0563d0aa83613311191e075a9b58861e80392914d61a21bad976 |
| APT28_2016-07_Invincea_Tunnel of Gov DNC Hack and the Russian XTunnel | Tunnel of Gov_ DNC Hack and the Russian XTunnel _ Invincea.pdf | b1b88f78c2f4393d437da4ce743ac5e8 | fb0cb4527efc48c90a2cd3e9e46ce59eaa280c85c50d7b680c98bb159c27881d |
| APT28 | APT28_2016-10_ESET_Observing the Comings and Goings | ||
| APT28_2016-10_ESET_Observing the Comings and Goings | eset-sednit-part-2.pdf | c3c278991ad051fbace1e2f3a4c20998 | f9ed13d5aa43c74287a936bf52772080fc26b5c62a805e19abceb20ef08ea5ff |
| APT28_2016-10_ESET_Observing the Comings and Goings | Sedreco-dropper | ||
| Sedreco-dropper | 4F895DB287062A4EE1A2C5415900B56E2CF15842 | 5363e5cc28687b7dd71f1e257eab2d5d | d403ded7c4acfffe8dc2a3ad8fb848f08388b4c3452104f6970835913d92166c |
| Sedreco-dropper | 87F45E82EDD63EF05C41D18AEDDEAC00C49F1AEE | 9617f3948b1886ebc95689c02d2cf264 | 378ef276eeaa4a29dab46d114710fc14ba0a9f964f6d949bcbc5ed3267579892 |
| Sedreco-dropper | 8EE6CEC34070F20FD8AD4BB202A5B08AEA22ABFA | 30cda69cf82637dfa2ffdc803bf2aead | 20ac1420eade0bdb464cd9f6d26a84094271b252c0650a7853721d8e928f6e6c |
| Sedreco-dropper | 9E779C8B68780AC860920FCB4A8E700D97F084EF | f686304cff9b35ea0d7647820ab525ba | 2c81023a146d2b5003d2b0c617ebf2eb1501dc6e55fc6326e834f05f5558c0ec |
| Sedreco-dropper | C23F18DE9779C4F14A3655823F235F8E221D0F6A | 9f82abbaebc1093a187f1887df2cf926 | ec2f14916e0b52fb727111962dff9846839137968e32269a82288aee9f227bd4 |
| Sedreco-dropper | E034E0D9AD069BAB5A6E68C1517C15665ABE67C9 | 6a24be8f61bcd789622dc55ebb7db90b | fb3a3339e2ba82cb3dcdc43d0e49e7b8a26ced3a587f5ee15a256aee062e6e05 |
| Sedreco-dropper | E17615331BDCE4AFA45E4912BDCC989EACF284BC | 5e93cf87040cf225ab5b5b9f9f0a0d03 | 6bbec6b2927325891cc008d3378d30941fe9d21e5c9bd6459e8e3ba8c78833c2 |
| APT28_2016-10_ESET_Observing the Comings and Goings | Sedreco_payload | ||
| Sedreco_payload | 04301B59C6EB71DB2F701086B617A98C6E026872 | cf30b7550f04a9372c3257c9b5cff3e9 | 37bf2c811842972314956434449fd294e793b43c1a7b37cfe41af4fcc07d329d |
| Sedreco_payload | 11AF174294EE970AC7FD177746D23CDC8FFB92D7 | 9422ca55f7fca4449259d8878ede5e47 | ba1c02aa6c12794a33c4742e62cbda3c17def08732f3fbaeb801f1806770b9a0 |
| Sedreco_payload | E3B7704D4C887B40A9802E0695BAE379358F3BA0 | a96f4b8ac7aa9dbf4624424b7602d4f7 | a9dc96d45702538c2086a749ba2fb467ba8d8b603e513bdef62a024dfeb124cb |
| APT28_2016-10_ESET_Observing the Comings and Goings | XAgent-LIN | ||
| XAgent-LIN | 7E33A52E53E85DDB1DC8DC300E6558735ACF10CE | fd8d1b48f91864dc5acb429a49932ca3 | dd8facad6c0626b6c94e1cc891698d4982782a5564aae696a218c940b7b8d084 |
| XAgent-LIN | 9444D2B29C6401BC7C2D14F071B11EC9014AE040 | 364ff454dcf00420cff13a57bcb78467 | 8bca0031f3b691421cb15f9c6e71ce193355d2d8cf2b190438b6962761d0c6bb |
| XAgent-LIN | ECDDA7ACA5C805E5BE6E0AB2017592439DE7E32C | e107c5c84ded6cd9391aede7f04d64c8 | fd8b2ea9a2e8a67e4cb3904b49c789d57ed9b1ce5bebfe54fe3d98214d6a0f61 |
| XAgent-LIN | F080E509C988A9578862665B4FCF1E4BF8D77C3E | 075b6695ab63f36af65f7ffd45cccd39 | 02c7cf55fd5c5809ce2dce56085ba43795f2480423a4256537bfdfda0df85592 |
| APT28_2016-10_ESET_Observing the Comings and Goings | XAgent-WIN | ||
| XAgent-WIN | 072933FA35B585511003F36E3885563E1B55D55A | 99b93cfcff258eb49e7af603d779a146 | c19d266af9e33dae096e45e7624ab3a3f642c8de580e902fec9dac11bcb8d3fd |
| XAgent-WIN | 082141F1C24FB49981CC70A9ED50CDA582EE04DD | 7a055cbe6672f77b2271c1cb8e2670b8 | 99d3f03fc6f048c74e58da6fb7ea1e831ba31d58194ad2463a7a6cd55da5f96b |
| XAgent-WIN | 08C4D755F14FD6DF76EC86DA6EAB1B5574DFBAFD | 26ac59dab32f6246e1ce3da7506d48fa | 5f6b2a0d1d966fc4f1ed292b46240767f4acb06c13512b0061b434ae2a692fa1 |
| XAgent-WIN | 0F04DAD5194F97BB4F1808DF19196B04B4AEE1B8 | 8b6d824619e993f74973eedfaf18be78 | 972e907a901a7716f3b8f9651eadd65a0ce09bbc78a1ceacff6f52056af8e8f4 |
| XAgent-WIN | 3403519FA3EDE4D07FB4C05D422A9F8C026CEDBF | 113cc4a88fd28ea4398e312093a6a4d5 | ddab96e4a8e909065e05c4b6a73ba351ea45ad4806258f41ac3cecbcae8671a6 |
| XAgent-WIN | 499FF777C88AEACBBAA47EDDE183C944AC7E91D2 | ea726d3e8f6516807366584f3c5b5e2a | 82c4e9bc100533482a15a1d756d55e1a604d330eff8fbc0e13c4b166ac2c9bd3 |
| XAgent-WIN | 4B74C90C9D9CE7668AA9EB09978C1D8D4DFDA24A | 409848dabfd110f4d373dd0a97ff708e | 24e11c80f1d4c1e9db654d54cc784db6b5f4a126f9fe5e26c269fdc4009c8f29 |
| XAgent-WIN | 4BC32A3894F64B4BE931FF20390712B4EC605488 | 57cc08213ab8b6d4a538e4568d00a123 | b23193bff95c4e65af0c9848036eb80ef006503a78be842e921035f8d77eb5de |
| XAgent-WIN | 5F05A8CB6FEF24A91B3BD6C137B23AB3166F39AE | 9ca6ead1384953d787487d399c23cb41 | 07393ac2e890772f70adf9e8d3aa07ab2f98e2726e3be275276dadd00daf5fc6 |
| XAgent-WIN | 71636E025FA308FC5B8065136F3DD692870CB8A4 | 96ed0a7976e57ae0bb79dcbd67e39743 | ea957d663dbc0b28844f6aa7dfdc5ac0110a4004ac46c87d0f1aa943ef253cfe |
| XAgent-WIN | 780AA72F0397CB6C2A78536201BD9DB4818FA02A | effd7b2411975447fd36603445b380c7 | d0e019229493a1cfb3ffc918a2d8ffcbaee31f9132293c95b1f8c1fd6d595054 |
| XAgent-WIN | A70ED3AE0BC3521E743191259753BE945972118B | 9a66142acfc7739f78c23ab1252db45b | 715f69916db9ff8fedf6630307f4ebb84aae6653fd0e593036517c5040d84dbe |
| XAgent-WIN | BAA4C177A53CFA5CC103296B07B62565E1C7799F | 9d1a09bb98bf1ee31f390b60b0cf724d | dea4e560017b4da05e8fd0a03ba74239723349934ee8fbd201a79be1ecf1c32d |
| XAgent-WIN | C18EDCBA2C31533B7CDB6649A970DCE397F4B13C | 4265f6e8cc545b925912867ec8af2f11 | fc2dbfda41860b2385314c87e81f1ebb4f9ae1106b697e019841d8c3bf402570 |
| XAgent-WIN | C2E8C584D5401952AF4F1DB08CF4B6016874DDAC | 078755389b98d17788eb5148e23109a6 | 54c4ce98970a44f92be748ebda9fcfb7b30e08d98491e7735be6dd287189cea3 |
| XAgent-WIN | D00AC5498D0735D5AE0DEA42A1F477CF8B8B0826 | 12a9fff59de1663dec1b45ea2ede22f5 | 68065abd6482405614d245537600ea60857c6ec9febac4870486b5227589d35c |
| XAgent-WIN | D0DB619A7A160949528D46D20FC0151BF9775C32 | ee64d3273f9b4d80020c24edcbbf961e | e031299fa1381b40c660b8cd831bb861654f900a1e2952b1a76bedf140972a81 |
| XAgent-WIN | E816EC78462B5925A1F3EF3CDB3CAC6267222E72 | 404eb3f7554392e85e56aed414db8455 | 94c220653ea7421c60e3eafd753a9ae9d69b475d61230f2f403789d326309c24 |
| XAgent-WIN | F1EE563D44E2B1020B7A556E080159F64F3FD699 | 58ca9243d35e529499dd17d27642b419 | bebe0be0cf8349706b2feb789572e035955209d5bf5d5fea0e5d29a7fbfdc7c4 |
| APT28_2016-10_ESET_Observing the Comings and Goings | Xtunnel | ||
| Xtunnel | 0450AAF8ED309CA6BAF303837701B5B23AAC6F05 | 800af1c9d341b846a856a1e686be6a3e | 566ab945f61be016bfd9e83cc1b64f783b9b8deb891e6d504d3442bc8281b092 |
| Xtunnel | 067913B28840E926BF3B4BFAC95291C9114D3787 | 02522ce47a8db9544f8877dace7e0833 | d2a6064429754571682f475b6b67f36526f1573d846182aab3516c2637fa1e81 |
| Xtunnel | 1535D85BEE8A9ADB52E8179AF20983FB0558CCB3 | 4ac8d16ff796e825625ad1861546e2e8 | 8c488b029188e3280ed3614346575a4a390e0dda002bca08c0335210a6202949 |
| Xtunnel | 42DEE38929A93DFD45C39045708C57DA15D7586C | ae4ded48da0766d237ce2262202c3c96 | a2c9041ee1918523e67dbaf1c514f98609d4dbe451ba08657653bb41946fc89d |
| Xtunnel | 8F4F0EDD5FB3737914180FF28ED0E9CCA25BF4CC | e766e048bd222cfd2b9cc1bf24125dac | 1289ee3d29967f491542c0bdeff6974aad6b37932e91ff9c746fb220d5edb407 |
| Xtunnel | 982D9241147AAACF795174A9DAB0E645CF56B922 | 0ebfac6dba63ff8b35cbd374ef33323a | c9ef265fc0a174f3033ff21b8f0274224eb7154dca97f15cba598952be2fbace |
| Xtunnel | 99B454262DC26B081600E844371982A49D334E5E | ac3e087e43be67bdc674747c665b46c2 | a979c5094f75548043a22b174aa10e1f2025371bd9e1249679f052b168e194b3 |
| Xtunnel | C637E01F50F5FBD2160B191F6371C5DE2AC56DE4 | b2dc7c29cbf8d71d1dd57b474f1e04b9 | c6a9db52a3855d980a7f383dbe2fb70300a12b7a3a4f0a995e2ebdef769eaaca |
| Xtunnel | C91B192F4CD47BA0C8E49BE438D035790FF85E70 | 672b8d14d1d3e97c24baf69d50937afc | 1c8869abf756e77e1b6d7d0ad5ca8f1cdce1a111315c3703e212fb3db174a6d5 |
| Xtunnel | CDEEA936331FCDD8158C876E9D23539F8976C305 | 5e70a5c47c6b59dae7faf0f2d62b28b3 | 730a0e3daf0b54f065bdd2ca427fbe10e8d4e28646a5dc40cbcfb15e1702ed9a |
| Xtunnel | DB731119FCA496064F8045061033A5976301770D | 34651f2df01b956f1989da4b3ea40338 | 60ee6fdca66444bdc2e4b00dc67a1b0fdee5a3cd9979815e0aab9ce6435262c6 |
| Xtunnel | DE3946B83411489797232560DB838A802370EA71 | 1d1287d4a3ba5d02cca91f51863db738 | 4dd8ab2471337a56b431433b7e8db2a659dc5d9dc5481b4209c4cddd07d6dc2b |
| Xtunnel | E945DE27EBFD1BAF8E8D2A81F4FB0D4523D85D6A | cd1c521b6ae08fc97e3d69f242f00f9e | d2e947a39714478983764b270985d2529ff682ffec9ebac792158353caf90ed3 |
| APT28 | APT28_2016-10_ESET_Sednit A Mysterious Downloader | ||
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 1CC2B6B208B7687763659AEB5DCB76C5C2FBBF26.scr_ | 006b418307c534754f055436a91848aa | 6507caba5835cad645ae80a081b98284032e286d97dabb98bbfeb76c3d51a094 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 49ACBA812894444C634B034962D46F986E0257CF.exe_ | 23ae20329174d44ebc8dbfa9891c6260 | 3e23201e6c52470e73a92af2ded12e6a5d1ad39538f41e762ca1c4b8d93c6d8d |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 4C9C7C4FD83EDAF7EC80687A7A957826DE038DD7.exe_ | 0eefeaf2fb78ebc49e7beba505da273d | 6ccc375923a00571dffca613a036f77a9fc1ee22d1fddffb90ab7adfbb6b75f1 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 4F92D364CE871C1AEBBF3C5D2445C296EF535632.exe_ | 9227678b90869c5a67a05defcaf21dfb | 79a508ba42247ddf92accbf5987b1ffc7ba20cd11806d332979d8a8fe85abb04 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 516EC3584073A1C05C0D909B8B6C15ECB10933F1.exe_ | 607a7401962eaf78b93676c9f5ca6a26 | ecd2c8e79554f226b69bed7357f61c75f1f1a42f1010d7baa72abe661a6c0587 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 593D0EB95227E41D299659842395E76B55AA048D.exe_ | 6cd2c953102792b738664d69ce41e080 | a13aa88c32eb020071c2c92f5364fd98f6dead7bcf71320731f05cd0a34a59db |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 593D0EB95227E41D299659842395E76B55AA048D_dll_ | 6cd2c953102792b738664d69ce41e080 | a13aa88c32eb020071c2c92f5364fd98f6dead7bcf71320731f05cd0a34a59db |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 5C132AE63E3B41F7B2385740B9109B473856A6A5.dll_ | 94ebc9ef5565f98b1aa1e97c6d35c2e0 | cfc60d5db3bfb4ec462d5e4bd5222f04d7383d2c1aec1dc2a23e3c74a166a93d |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 5FC4D555CA7E0536D18043977602D421A6FD65F9.exe_ | 81d9649612b05829476854bde71b8c3f | 1faf645c2b43cd78cc70df6bcbcd95e38f19d16ca2101de0b6a8fc31cac24c37 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 669A02E330F5AFC55A3775C4C6959B3F9E9965CF.exe_ | a0f212fd0f103ca8beaf8362f74903a2 | a50cb9ce1f01ea335c95870484903734ba9cd732e7b3db16cd962878bac3a767 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 6CAA48CD9532DA4CABD6994F62B8211AB9672D9E_bk.exe_ | 9df2ddb2631ff5439c34f80ace40cd29 | f18fe2853ef0d4898085cc5581ae35b83fc6d1c46563dbc8da1b79ef9ef678eb |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 7394EA20C3D510C938EF83A2D0195B767CD99ED7_x32.dll_ | d70f4e9d55698f69c5f63b1a2e1507eb | 471fbdc52b501dfe6275a32f89a8a6b02a2aa9a0e70937f5de610b4185334668 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | 9F3AB8779F2B81CAE83F62245AFB124266765939.exe_ | 3430bf72d2694e428a73c84d5ac4a4b9 | b1900cb7d1216d1dbc19b4c6c8567d48215148034a41913cc6e59958445aebde |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | E8ACA4B0CFE509783A34FF908287F98CAB968D9E.exe_ | 991ffdbf860756a4589164de26dd7ccf | 44e8d3ffa0989176e62b8462b3d14ad38ede5f859fd3d5eb387050f751080aa2 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | EE788901CD804965F1CD00A0AFC713C8623430C4.exe_ | 93c589e9eaf3272bc0349d605b85c566 | f9c0303d07800ed7cba1394cd326bbe8f49c7c5e0e062be59a9749f6c51c6e69 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | EE788901CD804965F1CD00A0AFC713C8623430C46.exe_ | 93c589e9eaf3272bc0349d605b85c566 | f9c0303d07800ed7cba1394cd326bbe8f49c7c5e0e062be59a9749f6c51c6e69 |
| APT28_2016-10_ESET_Sednit A Mysterious Downloader | eset-sednit-part3.pdf | a7b4e01335aac544a12c6f88aab80cd9 | 2c7a60963b94b6fc924abdcb19da4d32f35c86cdfe2277b0081cd02c72435b48 |
| APT28 | APT28_2016-10_ESET_Sednit Approaching the Target | ||
| APT28_2016-10_ESET_Sednit Approaching the Target | 015425010BD4CF9D511F7FCD0FC17FC17C23EEC1 | c2a0344a2bbb29d9b56d378386afcbed | 63d0b28114f6277b901132bc1cc1f541a594ee72f27d95653c54e1b73382a5f6 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 0F7893E2647A7204DBF4B72E50678545573C3A10 | 35283c2e60a3cba6734f4f98c443d11f | da43d39c749c121e99bba00ce809ca63794df3f704e7ad4077094abde4cf2a73 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 10686CC4E46CF3FFBDEB71DD565329A80787C439 | d7c471729bc124babf32945eb5706eb6 | bc8fec92eee715e77c762693f1ae2bbcd6a3f3127f1226a847a8efdc272e2cbc |
| APT28_2016-10_ESET_Sednit Approaching the Target | 17661A04B4B150A6F70AFDABE3FD9839CC56BEE8 | a579d53a1d29684de6d2c0cbabd525c5 | 6562e2ac60afa314cd463f771fcfb8be70f947f6e2b314b0c48187eebb33dd82 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 21835AAFE6D46840BB697E8B0D4AAC06DEC44F5B | 211b7100fd799e9eaabeb13cfa446231 | 3d13f2e5b241168005425b15410556bcf26d04078da6b2ef42bc0c2be7654bf8 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 2663EB655918C598BE1B2231D7C018D8350A0EF9 | 540e4a7a28ca1514e53c2564993d8d87 | 31dd3e3c05fabbfeafbcb7f5616dba30bbb2b1fc77dba6f0250a2c3270c0dd6b |
| APT28_2016-10_ESET_Sednit Approaching the Target | 2C86A6D6E9915A7F38D119888EDE60B38AB1D69D | 56e011137b9678f1fcc54f9372198bae | 69d5123a277dc1f618be5edcc95938a0df148c856d2e1231a07e2743bd683e01 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 351C3762BE9948D01034C69ACED97628099A90B0 | 83cf67a5d2e68f9c00fbbe6d7d9203bf | 853dbbba09e2463c45c0ad913d15d67d15792d888f81b4908b2216859342aa04 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 3956CFE34566BA8805F9B1FE0D2639606A404CD4 | dffb22a1a6a757443ab403d61e760f0c | 0356f5fa9907ea060a7d6964e65f019896deb1c7e303b7ba04da1458dc73a842 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 4D5E923351F52A9D5C94EE90E6A00E6FCED733EF | 6159c094a663a171efd531b23a46716d | e00eaf295a28f5497dbb5cb8f647537b6e55dd66613505389c24e658d150972c |
| APT28_2016-10_ESET_Sednit Approaching the Target | 4FAE67D3988DA117608A7548D9029CADDBFB3EBF | c6a80316ea97218df11e11125337233a | b0b3f0d6e6c593e2a2046833080574f98566c48a1eda865b2e110cd41bf31a31 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 51B0E3CD6360D50424BF776B3CD673DD45FD0F97 | 973e0c922eb07aad530d8a1de19c7755 | 7c4101caf833aa9025fec4f04a637c049c929459ad3e4023ba27ac72bde7638d |
| APT28_2016-10_ESET_Sednit Approaching the Target | 51E42368639D593D0AE2968BD2849DC20735C071 | dfc836e035cb6c43ce26ed870f61d7e8 | 13468ebe5d47d57d62777043c80784cbf475fb2de1df4546a307807bd2376b45 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 5C3E709517F41FEBF03109FA9D597F2CCC495956 | ac75fd7d79e64384b9c4053b37e5623f | 0ac7b666814fd016b3d21d7812f4a272104511f90ca666fa13e9fb6cefa603c7 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 63D1D33E7418DAF200DC4660FC9A59492DDD50D9 | 2d4eaa0331abbc6d867f5f979b2c890d | b4f755c91c2790f4ab9bac4ee60725132323e13a2688f3d8939ae9ed4793d014 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 69D8CA2A02241A1F88A525617CF18971C99FB63B | ed601bbd4dd0e267afb0be840cb27c90 | 4c52957270e63efa4b81a1c6551c706b82951f019b682219096e67182a727eab |
| APT28_2016-10_ESET_Sednit Approaching the Target | 6FB3FD8C2580C84314B14510944700144A9E31DF | f7ee38ca49cd4ae35824ce5738b6e587 | 63911ebce691c4b7c9582f37f63f6f439d2ce56e992bfbdcf812132512e753eb |
| APT28_2016-10_ESET_Sednit Approaching the Target | 80DCA565807FA69A75A7DD278CEF1DAAEE34236E | 9863f1efc5274b3d449b5b7467819d28 | 0abda721c4f1ca626f5d8bd2ce186aa98b197ca68d53e81cf152c32230345071 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 842B0759B5796979877A2BAC82A33500163DED67 | 291af793767f5c5f2dc9c6d44f1bfb59 | f50791f9909c542e4abb5e3f760c896995758a832b0699c23ca54b579a9f2108 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 8F99774926B2E0BF85E5147AACA8BBBBCC5F1D48 | c2988e3e4f70d5901b234ff1c1363dcc | 69940a20ab9abb31a03fcefe6de92a16ed474bbdff3288498851afc12a834261 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 90C3B756B1BB849CBA80994D445E96A9872D0CF5 | 21d63e99ed7dcd8baec74e6ce65c9ef3 | dfa8a85e26c07a348a854130c652dcc6d29b203ee230ce0603c83d9f11bbcacc |
| APT28_2016-10_ESET_Sednit Approaching the Target | 99F927F97838EB47C1D59500EE9155ADB55B806A | 07c8a0a792a5447daf08ac32d1e283e8 | 8f0674cb85f28b2619a6e0ddc74ce71e92ce4c3162056ef65ff2777104d20109 |
| APT28_2016-10_ESET_Sednit Approaching the Target | 9FC43E32C887B7697BF6D6933E9859D29581EAD0 | a3c757af9e7a9a60e235d08d54740fbc | bf28267386a010197a50b65f24e815aa527f2adbc53c609d2b2a4f999a639413 |
| APT28_2016-10_ESET_Sednit Approaching the Target | A43EF43F3C3DB76A4A9CA8F40F7B2C89888F0399 | 7c2b1de614a9664103b6ff7f3d73f83d | c2551c4e6521ac72982cb952503a2e6f016356e02ee31dea36c713141d4f3785 |
| APT28_2016-10_ESET_Sednit Approaching the Target | A5FCA59A2FAE0A12512336CA1B78F857AFC06445 | f1d3447a2bff56646478b0adb7d0451c | 5a414a39851c4e22d4f9383211dfc080e16e2caffd90fa06dcbe51d11fdb0d6c |
| APT28_2016-10_ESET_Sednit Approaching the Target | A857BCCF4CC5C15B60667ECD865112999E1E56BA | 0c334645a4c12513020aaabc3b78ef9f | e1b1143c0003c6905227df37d40aacbaecc2be8b9d86547650fe11bd47ca6989 |
| APT28_2016-10_ESET_Sednit Approaching the Target | B4A515EF9DE037F18D96B9B0E48271180F5725B7 | afe09fb5a2b97f9e119f70292092604e | d93f22d46090bfc19ef51963a781eeb864390c66d9347e86e03bba25a1fc29c5 |
| APT28_2016-10_ESET_Sednit Approaching the Target | B7788AF2EF073D7B3FB84086496896E7404E625E | eda061c497ba73441994a30e36f55b1d | b1800cb1d4b755e05b0fca251b8c6da96bb85f8042f2d755b7f607cbeef58db8 |
| APT28_2016-10_ESET_Sednit Approaching the Target | B8AABE12502F7D55AE332905ACEE80A10E3BC399 | 91381cd82cdd5f52bbc7b30d34cb8d83 | 1a09ce8a9210d2530d6ce1d59bfae2ac617ac89558cdcdcac15392d176e70c8d |
| APT28_2016-10_ESET_Sednit Approaching the Target | C1EAE93785C9CB917CFB260D3ABF6432C6FDAF4D | 732fbf0a4ceb10e9a2254af59ae4f880 | 6236a1bdd76ed90659a36f58b3e073623c34c6436d26413c8eca95f3266cc6fc |
| APT28_2016-10_ESET_Sednit Approaching the Target | C2E8C584D5401952AF4F1DB08CF4B6016874DDAC | 078755389b98d17788eb5148e23109a6 | 54c4ce98970a44f92be748ebda9fcfb7b30e08d98491e7735be6dd287189cea3 |
| APT28_2016-10_ESET_Sednit Approaching the Target | C345A85C01360F2833752A253A5094FF421FC839 | 1219318522fa28252368f58f36820ac2 | fbd5c2cf1c1f17402cc313fe3266b097a46e08f48b971570ef4667fbfd6b7301 |
| APT28_2016-10_ESET_Sednit Approaching the Target | D3AA282B390A5CB29D15A97E0A046305038DBEFE | 18efc091b431c39d3e59be445429a7bc | eae782130b06d95f3373ff7d5c0977a8019960bdf80614c1aa7e324dc350428a |
| APT28_2016-10_ESET_Sednit Approaching the Target | D85E44D386315B0258847495BE1711450AC02D9F | c4ffab85d84b494e1c450819a0e9c7db | 500fa112a204b6abb365101013a17749ce83403c30cd37f7c6f94e693c2d492f |
| APT28_2016-10_ESET_Sednit Approaching the Target | D9989A46D590EBC792F14AA6FEC30560DFE931B1 | 8b031fce1d0c38d6b4c68d52b2764c7e | 4bcd11142d5b9f96730715905152a645a1bf487921dd65618c354281512a4ae7 |
| APT28_2016-10_ESET_Sednit Approaching the Target | E5FB715A1C70402774EE2C518FB0E4E9CD3FDCFF | 072c692783c67ea56da9de0a53a60d11 | c431ae04c79ade56e1902094acf51e5bf6b54d65363dfa239d59f31c27989fde |
| APT28_2016-10_ESET_Sednit Approaching the Target | E742B917D3EF41992E67389CD2FE2AAB0F9ACE5B | 7764499bb1c4720d0f1d302f15be792c | 63047199037892f66dc083420e2fc60655a770756848c1f07adc2eb7d4a385d0 |
| APT28_2016-10_ESET_Sednit Approaching the Target | ED9F3E5E889D281437B945993C6C2A80C60FDEDC | 2dfc90375a09459033d430d046216d22 | 261b0a5912965ea95b8ae02aae1e761a61f9ad3a9fb85ef781e62013d6a21368 |
| APT28_2016-10_ESET_Sednit Approaching the Target | F024DBAB65198467C2B832DE9724CB70E24AF0DD | 7b1bfd7c1866040e8f618fe67b93bea5 | df47a939809f925475bc19804319652635848b8f346fb7dfd8c95c620595fe9f |
| APT28_2016-10_ESET_Sednit Approaching the Target | F3D50C1F7D5F322C1A1F9A72FF122CAC990881EE | 77089c094c0f2c15898ff0f021945148 | eb6620442c3ab327f3ccff1cc6d63d6ffe7729186f7e8ac1dbbbfddd971528f0 |
| APT28_2016-10_ESET_Sednit Approaching the Target | F7608EF62A45822E9300D390064E667028B75DEA | 75f71713a429589e87cf2656107d2bfc | b6fff95a74f9847f1a4282b38f148d80e4684d9c35d9ae79fad813d5dc0fd7a9 |
| APT28_2016-10_ESET_Sednit Approaching the Target | eset-sednit-part1.pdf | bae0221feefb37e6b81f5ca893864743 | b31b27aa0808aea5b0e8823ecb07402c0c2bbf6818a22457e146c97f685162b4 |
| APT28 | APT28_2016-10_Sekoia_Rootkit analysisUse case on HideDRV | ||
| APT28_2016-10_Sekoia_Rootkit analysisUse case on HideDRV | 83E54CB97644DE7084126E702937F8C3A2486A2F_fsflt.sys_ | f8c8f6456c5a52ef24aa426e6b121685 | 4bfe2216ee63657312af1b2507c8f2bf362fdf1d63c88faba397e880c2e39430 |
| APT28_2016-10_Sekoia_Rootkit analysisUse case on HideDRV | 9F3AB8779F2B81CAE83F62245AFB124266765939_fsflt.1 | 3430bf72d2694e428a73c84d5ac4a4b9 | b1900cb7d1216d1dbc19b4c6c8567d48215148034a41913cc6e59958445aebde |
| APT28 | APT28_2017-02_Bitdefender_OSX_XAgent | ||
| APT28_2017-02_Bitdefender_OSX_XAgent | 70A1C4ED3A09A44A41D54C4FD4B409A5FC3159F6_XAgent_OSX | 4fe4b9560e99e33dabca553e2eeee510 | 2a854997a44f4ba7e307d408ea2d9c1d84dde035c5dab830689aa45c5b5746ea |
More articles
Feliratkozás:
Megjegyzések (Atom)